Optimizing Java XPath CPU and memory overhead by 98%
Dynatrace
MARCH 9, 2022
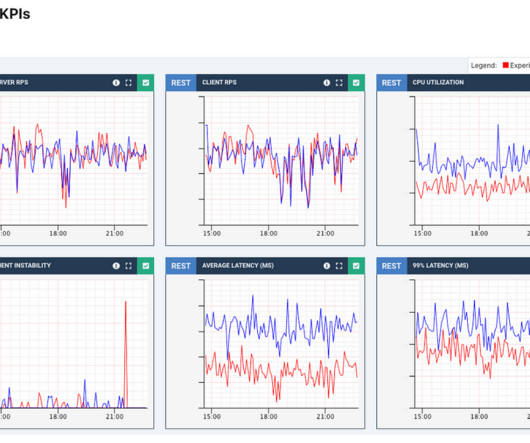
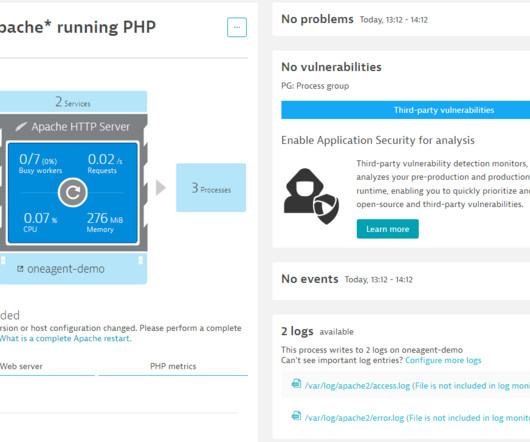
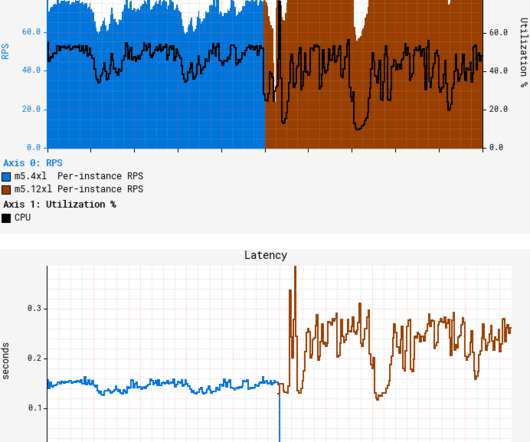
Therefore, it was unsurprising to see a huge spike in traffic for Family Visa enrollment via Metrash. The system saw up to 800 application requests per second – far more than anticipated. More worrisome was a spike in CPU usage, resulting in severe service disruption as backend processing systems crashed due to the spike in load.







































Let's personalize your content