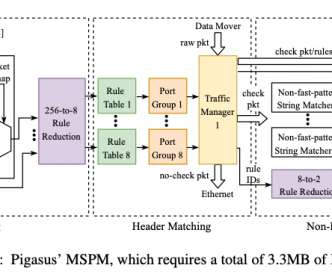
Dynatrace observability is now available for Red Hat OpenShift on the IBM® Power® architecture
Dynatrace
JULY 11, 2023
We’re delighted to share that IBM and Dynatrace have joined forces to bring the Dynatrace Operator, along with the comprehensive capabilities of the Dynatrace platform, to Red Hat OpenShift on the IBM Power architecture (ppc64le).













































Let's personalize your content