The Dynatrace journey toward DORA compliance
Dynatrace
APRIL 23, 2024
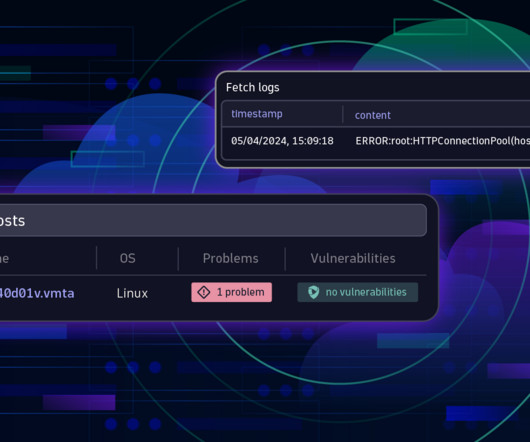
When operational disruptions strike—whether it’s a rogue server or a cyberattack—Dynatrace services remain in harmony. Imagine a dashboard that whispers, “Hey, there’s a vulnerability brewing in Server Room B.” Customer feedback shapes our compliance strategy. Imagine a symphony where every instrument knows its part.










































Let's personalize your content