Trade-offs under pressure: heuristics and observations of teams resolving internet service outages (Part 1)
The Morning Paper
JANUARY 21, 2020
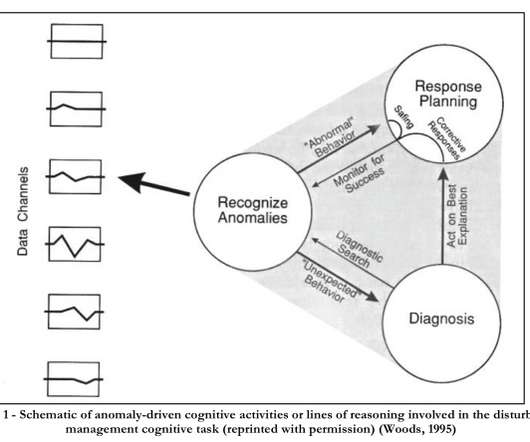
Trade-offs under pressure: heuristics and observations of teams resolving internet service outages , Allspaw, Masters thesis, Lund University, 2015. The Internet itself, over which these systems operate, is a dynamically distributed network spanning national borders and policies with no central coordinating agent.











































Let's personalize your content