AI techniques enhance and accelerate exploratory data analytics
Dynatrace
FEBRUARY 28, 2024
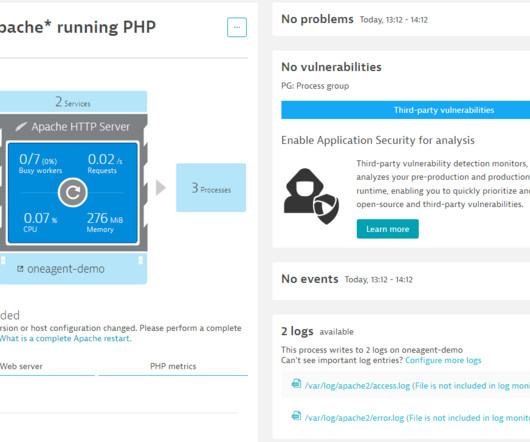
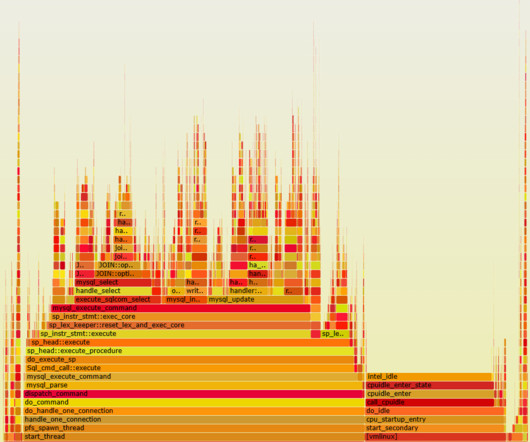
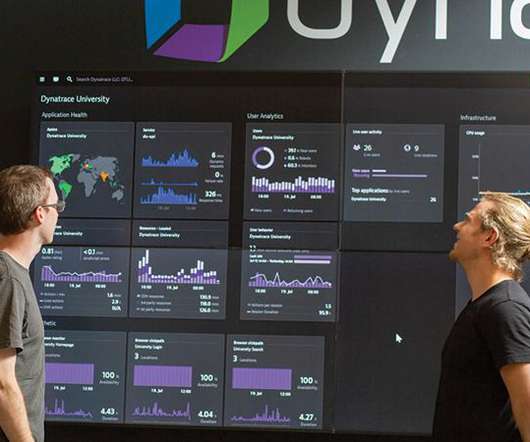
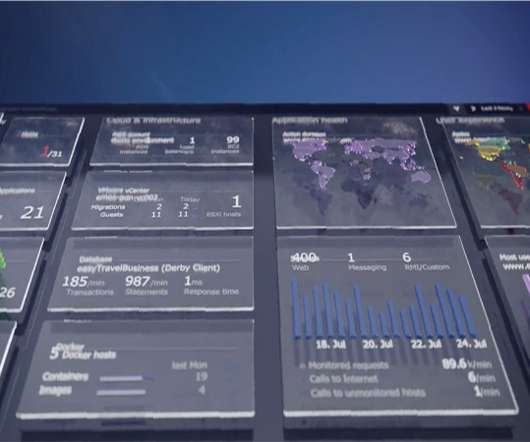
In a digital-first world, site reliability engineers and IT data analysts face numerous challenges with data quality and reliability in their quest for cloud control. Increasingly, organizations seek to address these problems using AI techniques as part of their exploratory data analytics practices.










































Let's personalize your content