What is application security monitoring?
Dynatrace
MARCH 20, 2024
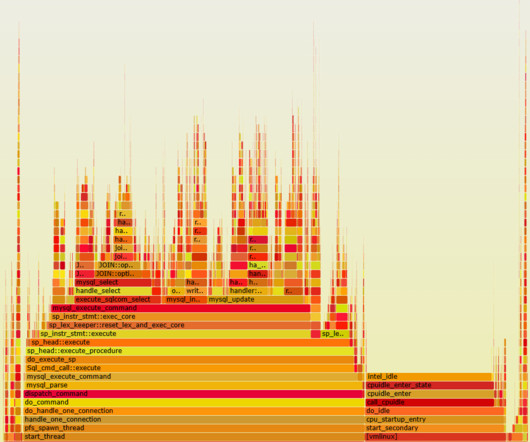
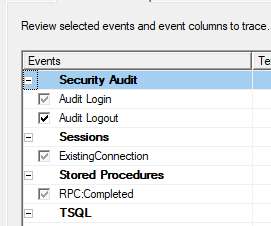
Continuously monitoring application behavior, network traffic, and system logs allows teams to identify abnormal or suspicious activities that could indicate a security breach. This approach can determine malicious activity and block it by monitoring the flow of data within the application, all the way from the user to the database.










































Let's personalize your content