The Three Cs: Concatenate, Compress, Cache
CSS Wizardry
OCTOBER 16, 2023
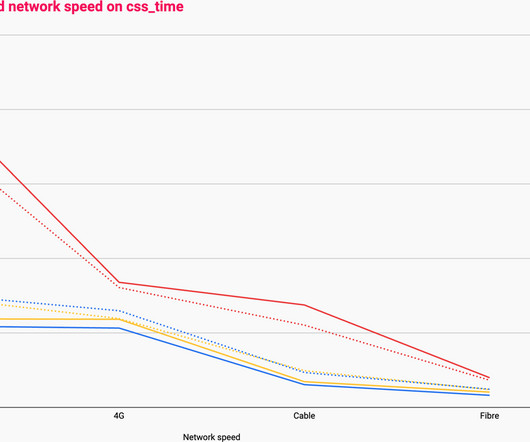
In this post, I’m going to break these processes down into each of: ? Caching them at the other end: How long should we cache files on a user’s device? Given that 66% of all websites (and 77% of all requests ) are running HTTP/2, I will not discuss concatenation strategies for HTTP/1.1 Cache This is the easy one.



























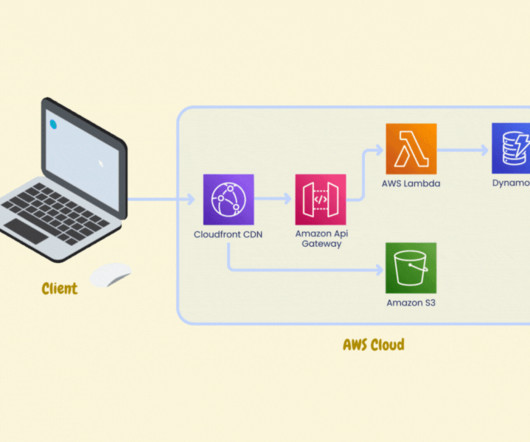
















Let's personalize your content