Dynatrace extends contextual analytics and AIOps for open observability
Dynatrace
JULY 29, 2021
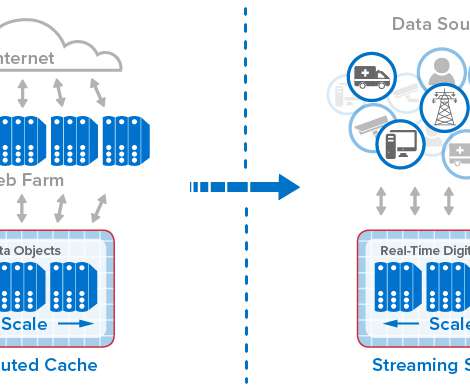
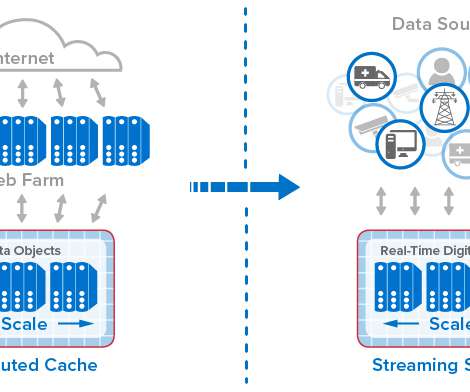
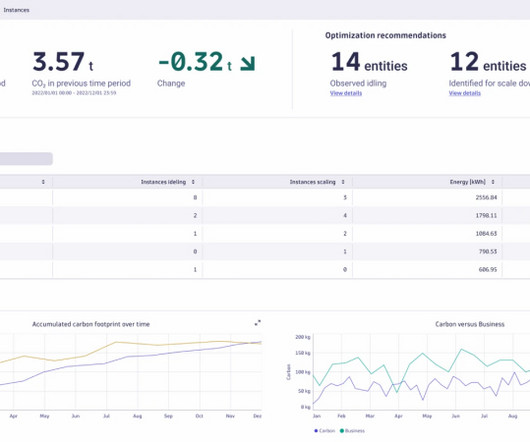
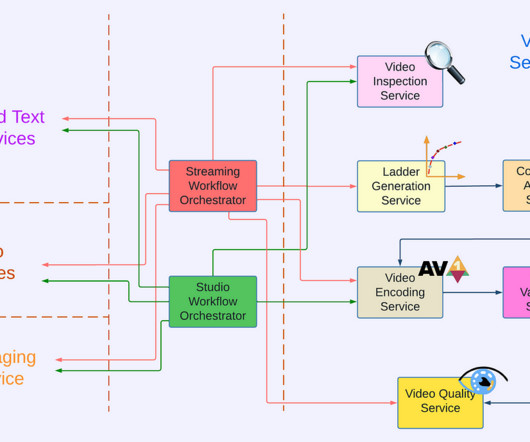
With extended contextual analytics and AIOps for open observability, Dynatrace now provides you with deep insights into every entity in your IT landscape, enabling you to seamlessly integrate metrics, logs, and traces—the three pillars of observability. Dynatrace extends its unique topology-based analytics and AIOps approach.











































Let's personalize your content