New Network Fallacies
Tim Kadlec
APRIL 18, 2019
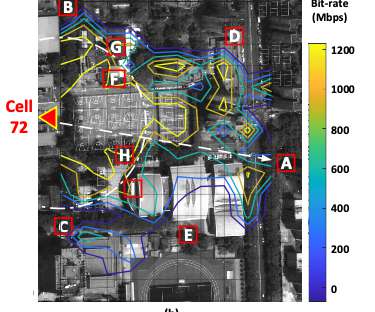
I remember reading articles about how 3G connectivity was going to transform performance and, more generally, the way we used the internet altogether. ” The fallacy of networks, or new devices for that matter, fixing our performance woes is old and repetitive. We’re not talking months in most places, but years.






























Let's personalize your content