Designing Better Links For Websites And Emails: A Guideline
Smashing Magazine
DECEMBER 6, 2021
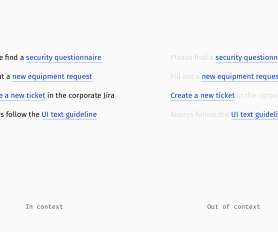
Designing Better Links For Websites And Emails: A Guideline. Designing Better Links For Websites And Emails: A Guideline. When a link is presented as “here” or “this,” it’s harder to aim it with a cursor or finger. A good practice for download links is to show the file format and size. Slava Shestopalov. Large preview ).



























Let's personalize your content