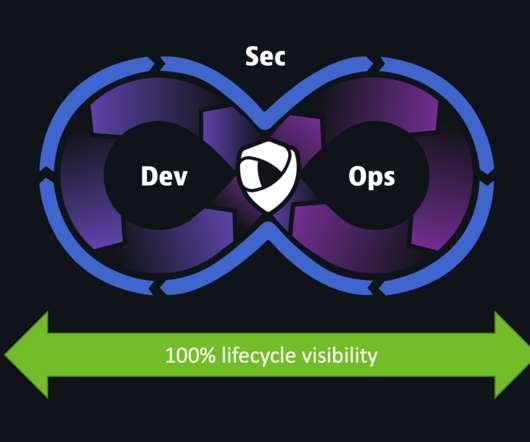
How to achieve the pillars of zero trust at federal agencies
Dynatrace
FEBRUARY 12, 2024
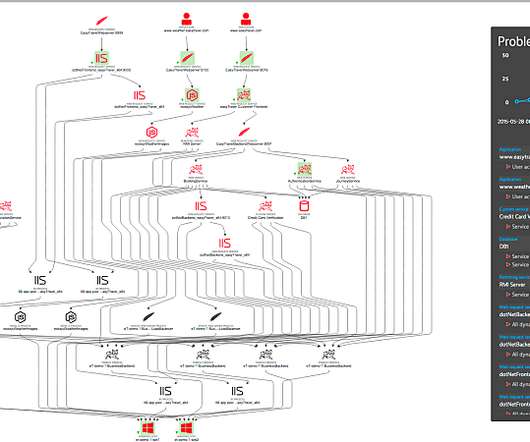
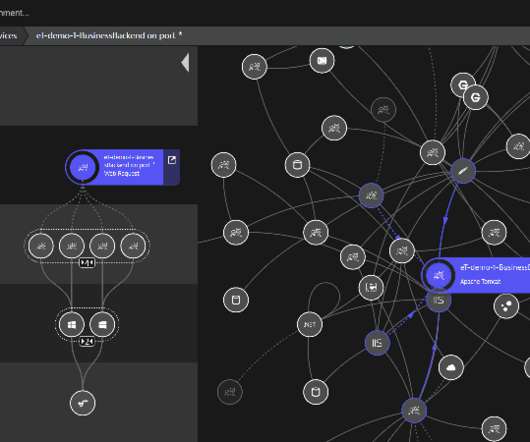
The OMB memo states that agencies must meet specific goals based on the five pillars of the Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model : identity, devices, networks, applications/workloads, and data. Discover more in the latest ebook. A quick refresher: what is zero trust?

































Let's personalize your content