RSA guide 2024: AI and security are top concerns for organizations in every industry
Dynatrace
MAY 2, 2024
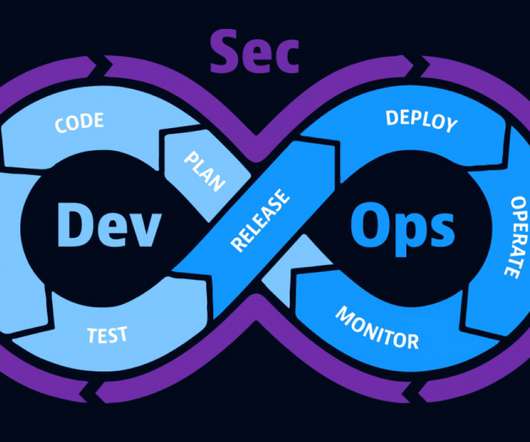
As organizations train generative AI systems with critical data, they must be aware of the security and compliance risks. Generative AI in IT operations – report Read the study to discover how artificial intelligence (AI) can help IT Ops teams accelerate processes, enable digital transformation, and reduce costs.











































Let's personalize your content