Practical API Design at Netflix, Part 1: Using Protobuf FieldMask
The Netflix TechBlog
SEPTEMBER 3, 2021
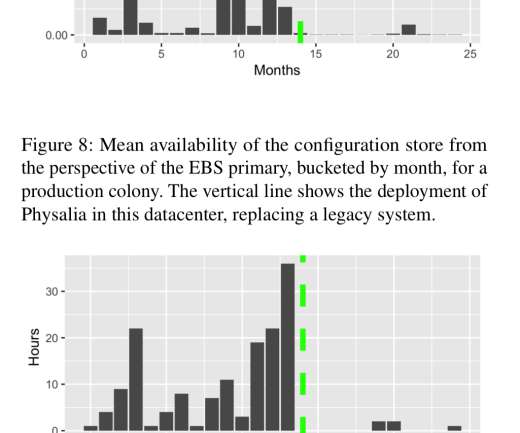
How can we achieve a similar functionality when designing our gRPC APIs? If the service knows which fields are important for the caller, it can make an informed decision about making expensive calls, starting resource-heavy computations, and/or calling the database. Our protobuf message definition (.proto Field names are not included.






























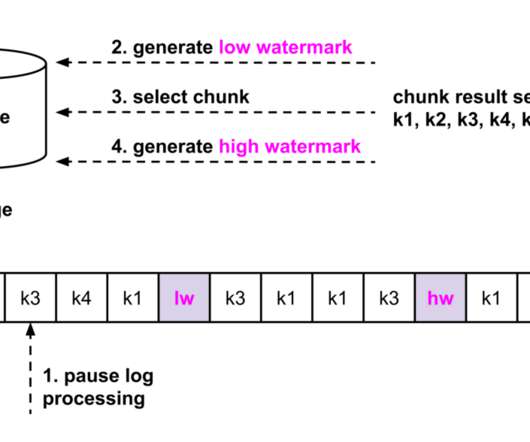
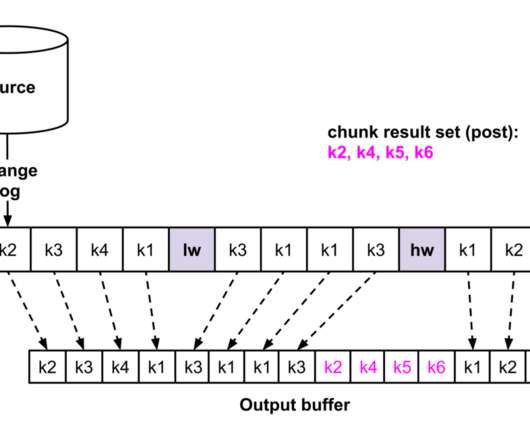







Let's personalize your content