Kubernetes: Challenges for observability platforms
Dynatrace
NOVEMBER 23, 2020
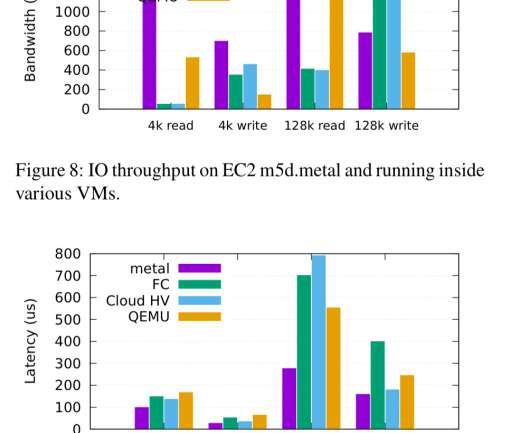
Nevertheless, there are related components and processes, for example, virtualization infrastructure and storage systems (see image below), that can lead to problems in your Kubernetes infrastructure. As a platform operator, you want to identify problems quickly and learn from them to prevent future outages.
















Let's personalize your content