Crucial Redis Monitoring Metrics You Must Watch
Scalegrid
JANUARY 25, 2024
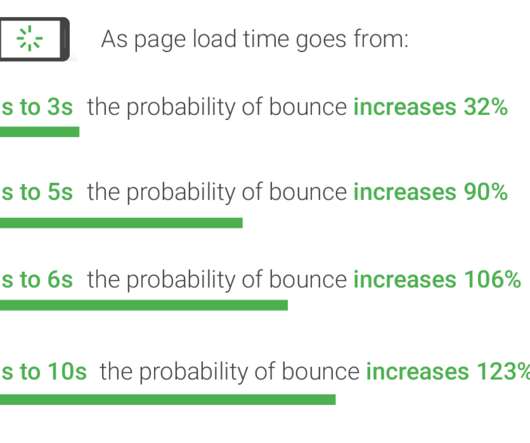
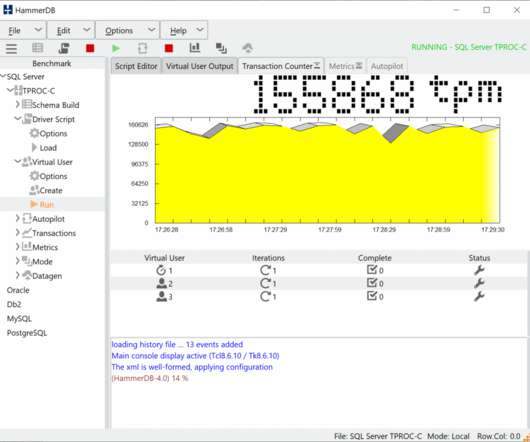
Key metrics like throughput, request latency, and memory utilization are essential for assessing Redis health, with tools like the MONITOR command and Redis-benchmark for latency and throughput analysis and MEMORY USAGE/STATS commands for evaluating memory. offers the Software Watchdog specifically designed for this purpose.

























Let's personalize your content