Getting ready! Part 2: A taste of what’s to come in the “Release Better Software Faster” track at Perform 2020
Dynatrace
DECEMBER 16, 2019
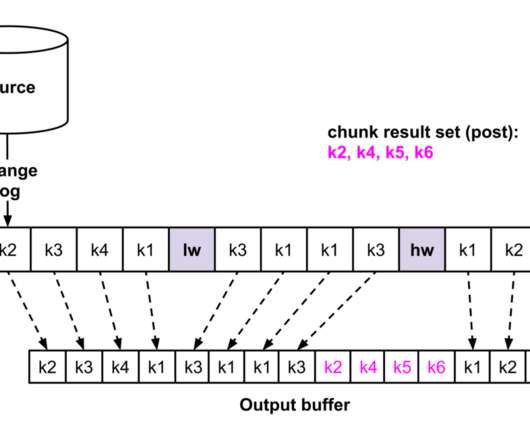
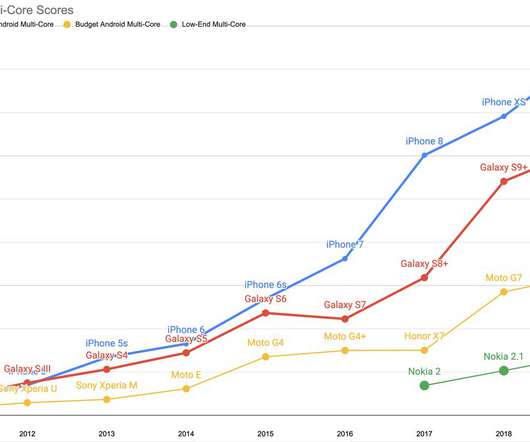
A taste of what’s to come at Perform 2020’s “Release Better Software Faster” track – we highlighted what you can expect to learn about best practices for sessions 1 – 4 at Perform 2020. They’ll cover scenarios where run-book automation is a fit, and where application architecture supporting “self-healing” is a fit.





















Let's personalize your content