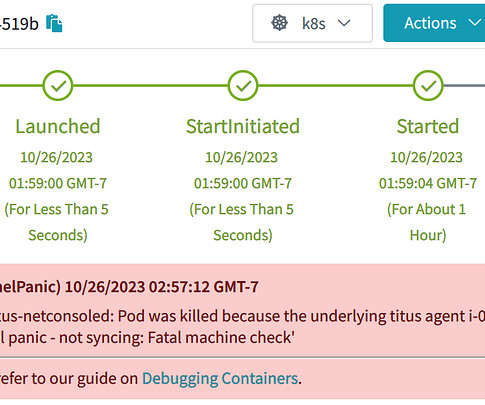
Kubernetes And Kernel Panics
The Netflix TechBlog
OCTOBER 27, 2023
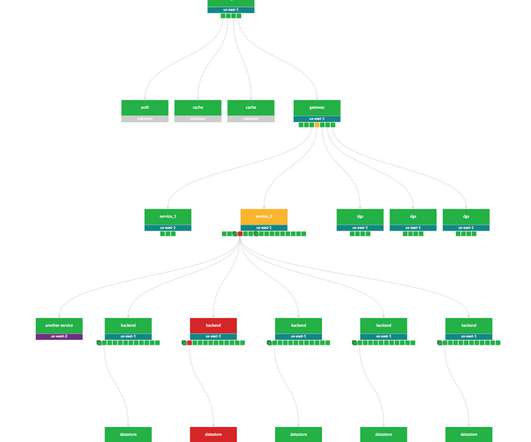
For that k8s node, find all the pods bound to it, annotate, then delete those pods (they are toast!). Adding an annotation (as opposed to patching the status) preserves the rest of the pod as-is for historical purposes. (We Upon kernel panic, lookup the k8s node object associated with the IP address of the incoming netconsole packet.
















Let's personalize your content