Three ways to optimize open source contributions
Dynatrace
JUNE 29, 2023
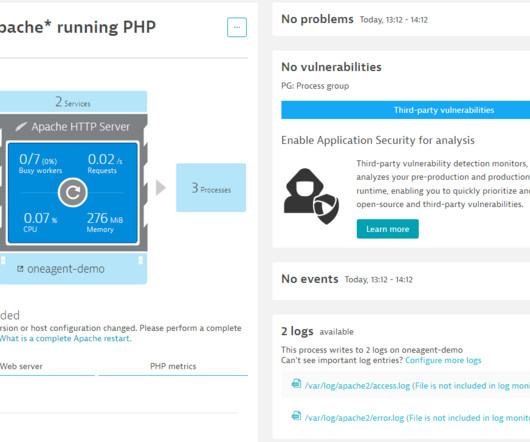
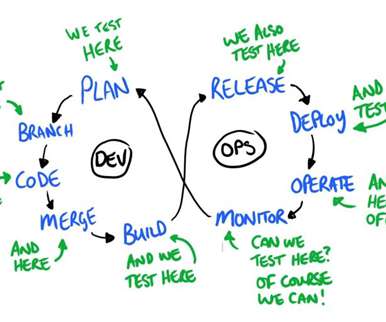
Because open source software (OSS) is taking over the world, optimizing open source contributions is becoming an essential competitive strategy. However, open source is not a panacea. These considerations are important if developers want to maximize the impact of their contributions to open source projects.


























Let's personalize your content