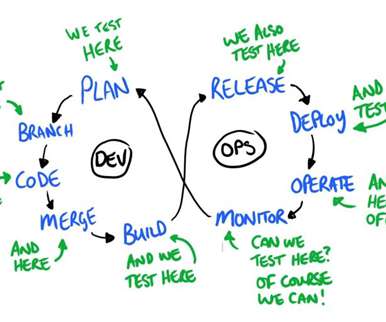
Monitoring-as-code through Dynatrace’s Open-Source Initiative
Dynatrace
JANUARY 13, 2021
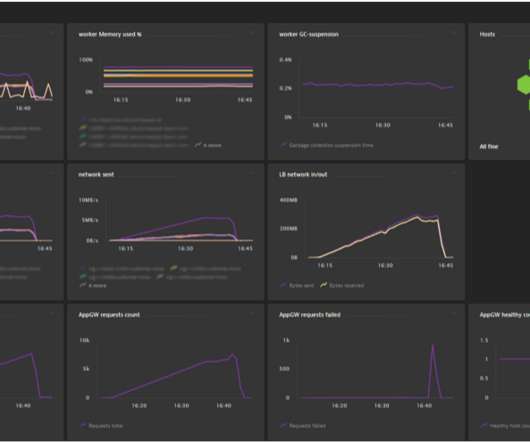
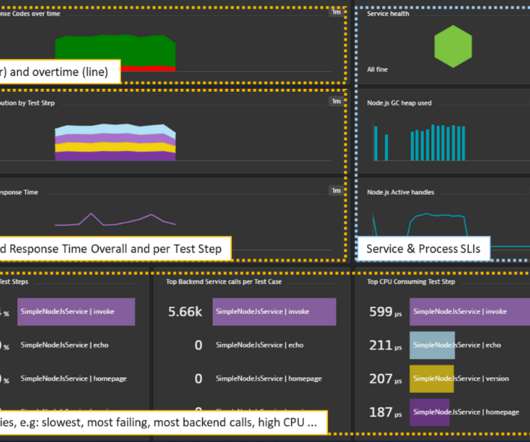
Dynatrace’s OneAgent automatically captures PurePaths and analyzes transactions end-to-end across every tier of your application technology stack with no code changes, from the browser all the way down to the code and database level. For instance, Zurich Insurance Company, applied this approach through Azure DevOps.




















Let's personalize your content