InfoSec 2022 guide: How DevSecOps practices drive organizational resilience
Dynatrace
JUNE 13, 2022
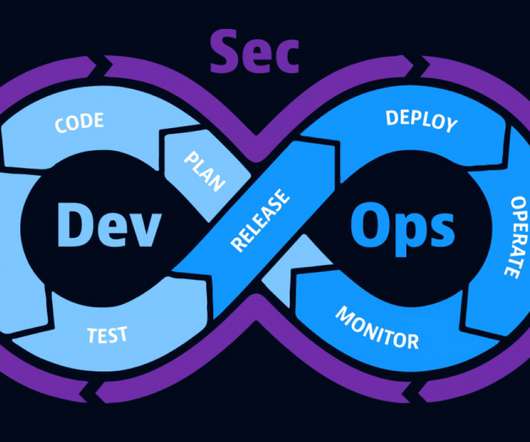
The conference’s theme recognizes that IT collaboration, DevSecOps culture, and business resilience are mutually reinforcing the role of DevSecOps teams in addressing application security threats, system downtime, and digital user experience issues. Spring4Shell vulnerabilities expose Java Spring Framework apps to exploitation.









































Let's personalize your content