Predictive CPU isolation of containers at Netflix
The Netflix TechBlog
JUNE 4, 2019
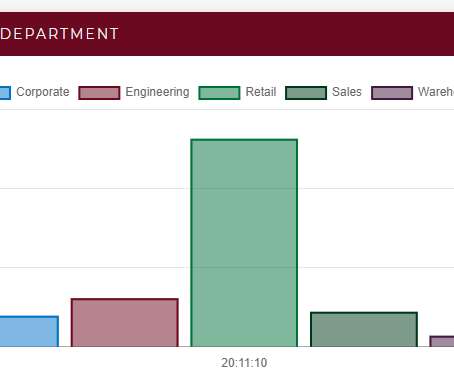
CFS is widely used and therefore well tested and Linux machines around the world run with reasonable performance. Resource allocation problems can be efficiently solved through a branch of mathematics called combinatorial optimization, used for example for airline scheduling or logistics problems. So why mess with it?









Let's personalize your content