Predictive CPU isolation of containers at Netflix
The Netflix TechBlog
JUNE 4, 2019
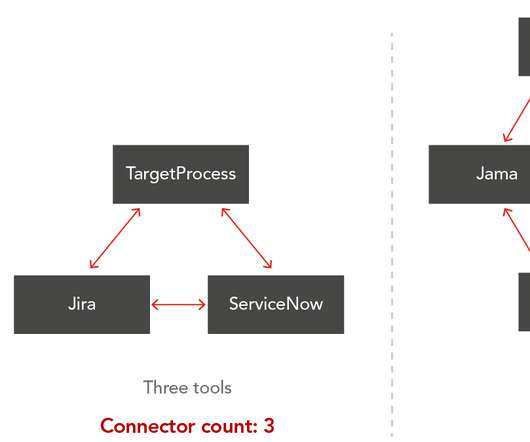
We were able to meaningfully improve both the predictability and performance of these containers by taking some of the CPU isolation responsibility away from the operating system and moving towards a data driven solution involving combinatorial optimization and machine learning. We formulate the problem as a Mixed Integer Program (MIP).









Let's personalize your content