What is log management? How to tame distributed cloud system complexities
Dynatrace
SEPTEMBER 8, 2022
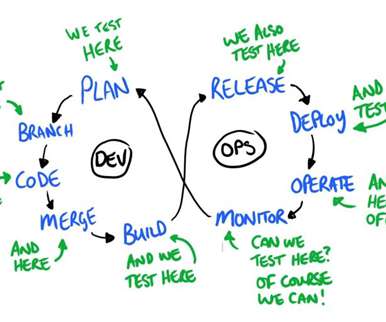
Log management is an organization’s rules and policies for managing and enabling the creation, transmission, analysis, storage, and other tasks related to IT systems’ and applications’ log data. In short, log management is how DevOps professionals and other concerned parties interact with and manage the entire log lifecycle.

















Let's personalize your content