InfoSec 2022 guide: How DevSecOps practices drive organizational resilience
Dynatrace
JUNE 13, 2022
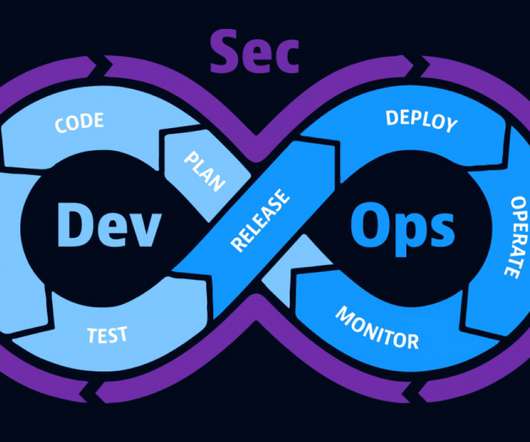
Dynatrace news. But with this speed, agility, and innovation come new challenges. Risks include performance problems and outages in cloud-native environments, application security vulnerabilities and poor digital experience for customers and other users. Security teams need their vulnerability management approach to be seamless.












Let's personalize your content