Vulnerability assessment: key to protecting applications and infrastructure
Dynatrace
OCTOBER 13, 2021
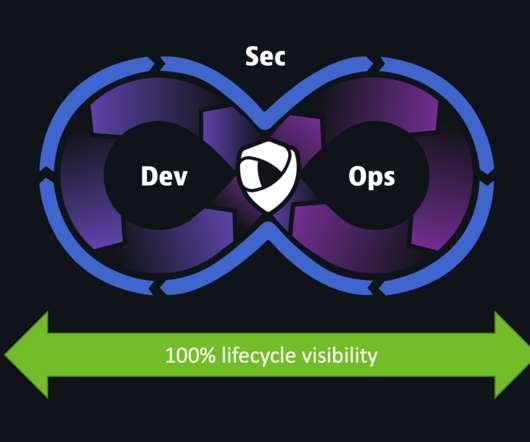
Protecting IT infrastructure, applications, and data requires that you understand security weaknesses attackers can exploit. Examples of such weaknesses are errors in application code, misconfigured network devices, and overly permissive access controls in a database. NMAP is an example of a well-known open-source network scanner.














Let's personalize your content