The anatomy of the Spring4Shell vulnerability and how to prevent its effects—and those of similar vulnerabilities
Dynatrace
APRIL 14, 2022
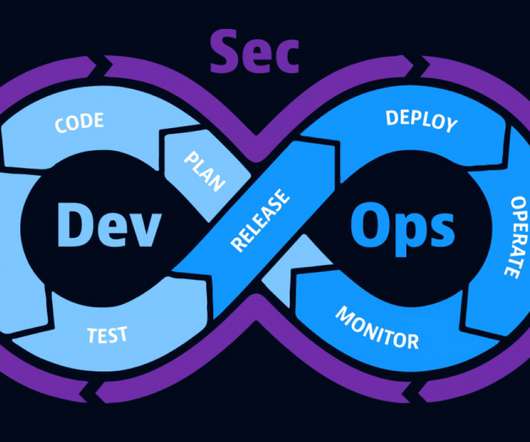
Dynatrace news. Spring4Shell is a critical vulnerability in the Spring Framework , which emerged in late March 2022. Because 60% of developers use Spring for their Java applications , many applications are potentially affected. What is the Spring Framework?














Let's personalize your content