Kubernetes vs Docker: What’s the difference?
Dynatrace
SEPTEMBER 29, 2021
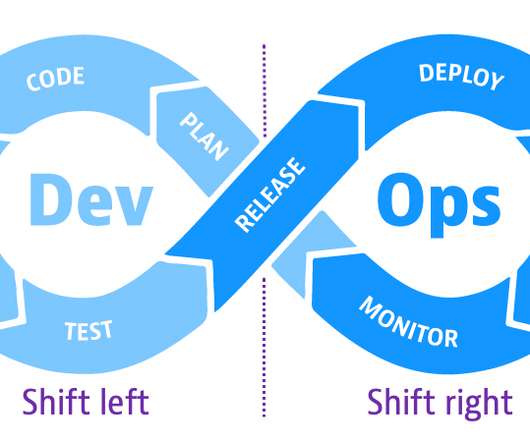
Think of containers as the packaging for microservices that separate the content from its environment – the underlying operating system and infrastructure. Just as people use Xerox as shorthand for paper copies and say “Google” instead of internet search, Docker has become synonymous with containers. What is Docker?












Let's personalize your content