Towards a Reliable Device Management Platform
The Netflix TechBlog
AUGUST 30, 2021
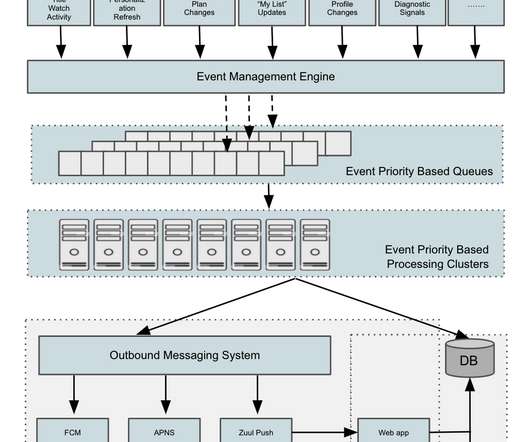
MQTT is an OASIS standard messaging protocol for the Internet of Things (IoT) and was designed as a highly lightweight yet reliable publish/subscribe messaging transport that is ideal for connecting remote devices with a small code footprint and minimal network bandwidth. This effectively ensures exactly-once processing on a per-event basis.















Let's personalize your content