Rising Tide Rents and Robber Baron Rents
O'Reilly
APRIL 23, 2024
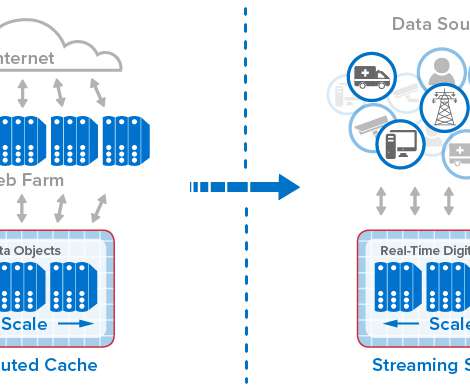
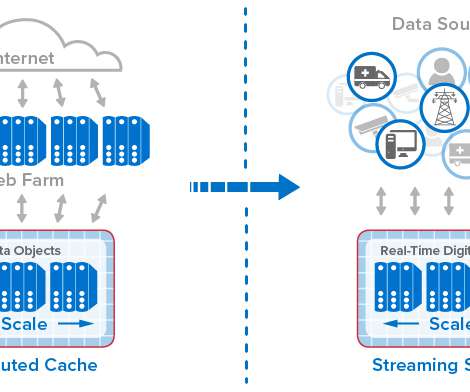
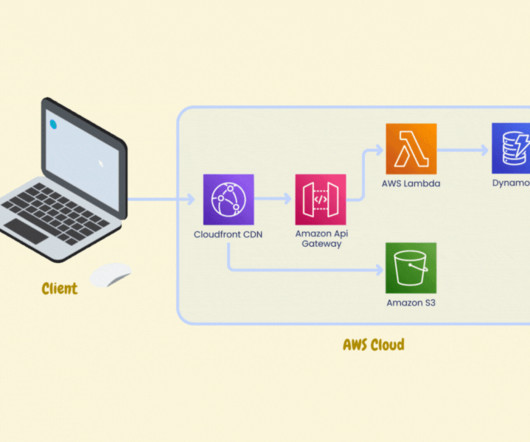
The answer can be found in the theory of economic rents, and in particular, in the kinds of rents that are collected by companies during different stages of the technology business cycle. Then the cycle begins again with a new class of competitors, who are forced to explore new, disruptive technologies that reset the entire market.











Let's personalize your content