The Speed of Time
Brendan Gregg
SEPTEMBER 25, 2021
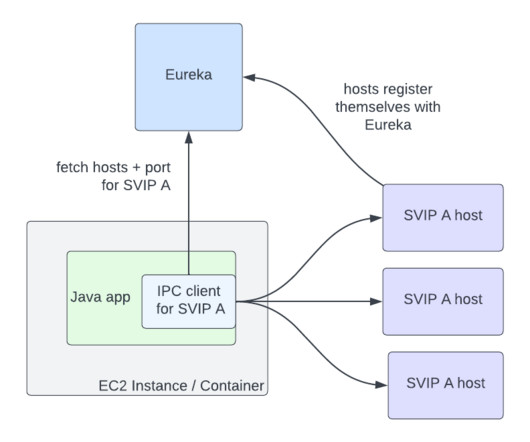
Since instances of both CentOS and Ubuntu were running in parallel, I could collect flame graphs at the same time (same time-of-day traffic mix) and compare them side by side. There's no Java stack—there should be a tower of green Java methods—instead there's only a single green frame or two. us on Centos and 0.68












Let's personalize your content