How to overcome the cloud observability wall
Dynatrace
DECEMBER 8, 2021
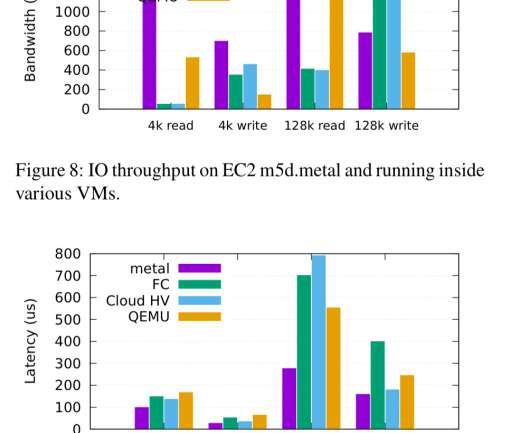
Let’s explore this concept as we look at the best practices and solutions you should keep in mind to overcome the wall and keep up with today’s fast-paced and intricate cloud landscape. When an application runs on a single large computing element, a single operating system can monitor every aspect of the system.










Let's personalize your content