What is cloud monitoring? How to improve your full-stack visibility
Dynatrace
JANUARY 11, 2023
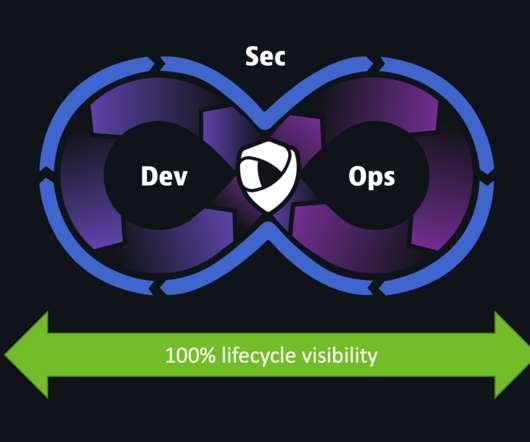
Cloud monitoring is a set of solutions and practices used to observe, measure, analyze, and manage the health of cloud-based IT infrastructure. Continuous cloud monitoring with automation provides clear visibility into the performance and availability of websites, files, applications, servers, and network resources.










Let's personalize your content