CDN Web Application Firewall (WAF): Your Shield Against Online Threats
Delivering content swiftly and securely is a challenge many websites grapple with. Unexpected threats lurk at every corner, causing disruptions and affecting user experiences. But what if there was a way to both speed up content delivery and ensure robust protection? Welcome to CDN Web Application Firewall (WAF) – the answer to many of these online dilemmas. Dive in as we explore how CDN WAF stands as a bulwark against online threats while ensuring a seamless web experience.

What is WAF?
WAF stands for Web Application Firewall. Let's break it down using a simple analogy:
Imagine you own a special kind of mailbox. Instead of just receiving letters, it also receives parcels, packages, and even gifts. But not all of these are meant for you; some could be scams, spam, or even dangerous items.
This is where WAF comes in! Think of WAF as the security guard for your special mailbox. It checks each item that arrives and ensures that only the safe and intended items reach you.
In a more technical sense:
- WAF is built to handle malicious HTTP requests. It acts like a shield for web applications, ensuring that only legitimate requests get through.
- When talking about how and where WAF operates, we refer to the OSI Model. The OSI Model is like a layer cake of how data moves through networks. WAF operates at the application level of this model.
This means it specifically looks at the content of the data (like the writing inside our letters from the analogy) rather than just the envelope.
So, what is the difference between a Firewall at the application level and network level?
- Network-level Firewalls: Think of these as the fences or gates around a property. They check who's coming and going based on broad criteria, like the type of vehicle or the road they're using.
In technical terms, network-level firewalls regulate access by blocking or permitting traffic based on predefined rules. They mainly focus on where data is coming from and where it's going. - Application-level Firewalls (like WAF): These are like the security checks at the entrance of a special event or building. They inspect the details, like the actual invitation or the ID of a person. They are more concerned with the content and specifics of the data.
Application-level security involves techniques like authentication, encryption, and input validation to protect the data and functionality of applications.
How Does WAF Work?
At its core, WAF operates by adhering to a rulebook—a comprehensive list of conditions that dictate how to handle incoming web traffic. When a request comes in, WAF evaluates it against these rules to determine whether it's a friend or a foe.
This rulebook is a dynamic entity that can be customized or managed through vendors.
Custom Rules

Let's get into custom rules first. Custom rules give you the flexibility to tailor your WAF according to your specific security needs. You're in the driver's seat, dictating what constitutes a threat for your particular application.
For instance, let's say you operate an e-commerce site and you've noticed a pattern of fraudulent transactions originating from a particular IP range. Custom rules enable you to block or flag traffic from that specific range, adding an extra layer of security that generic rule sets may not offer.
Managed Rules: Vendor-Managed, OWASP, and More

On the flip side, managed rules are sets of predefined conditions managed by third-party vendors. These are especially useful if you don't have the time or expertise to create your own custom rules. Vendors frequently update these rule sets to adapt to new security threats, offering you a hands-off approach to maintaining a robust defense.
Popular managed rule sets include those conforming to the Open Web Application Security Project (OWASP) guidelines. OWASP provides a baseline defense against the most critical web application security risks, such as SQL injection, cross-site scripting, and more.
What Happens When a Rule Triggers?
After WAF evaluates an incoming request based on these rules, it takes specific actions. These can range from allowing the request to pass through to blocking it entirely, or even diverting it to a CAPTCHA challenge to confirm its legitimacy.
The action isn't arbitrary; it's defined by the specific rule that the request triggers. For example, if a request activates a rule designed to block SQL injection attempts, the WAF might automatically block that request, preventing it from reaching your web application.
Security Flywheel
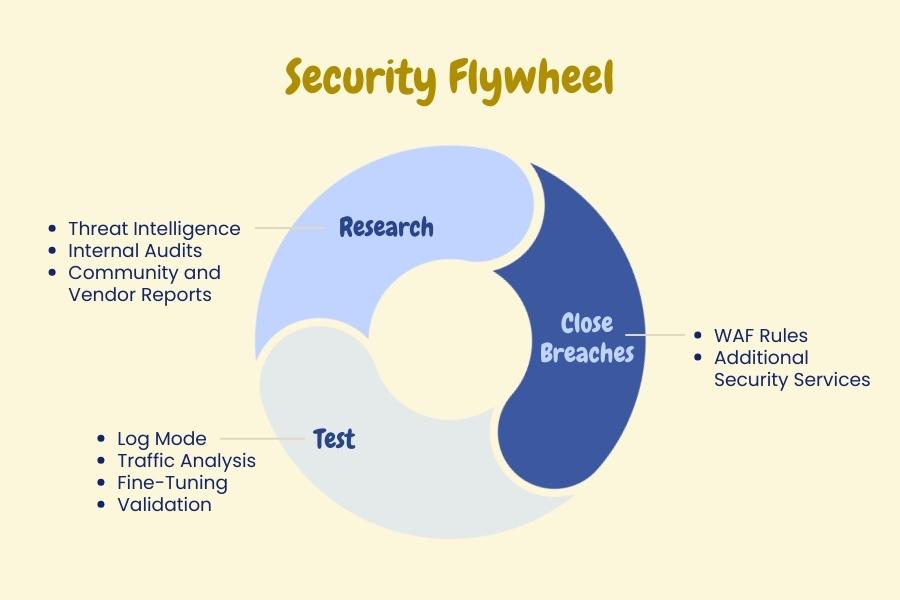
When it comes to fortifying web applications, think of security as a flywheel—an ever-revolving cycle that gains momentum with each turn. It's an ongoing, iterative process. Let's break down this Security Flywheel into its core components:
Research, Close Breaches, and Test. Each is crucial, and they all feed into each other to create a robust, responsive, and resilient security mechanism.
Research
In the dynamic world of the Internet, new threats are as constant as the rising sun. Cybercriminals are endlessly creative, exploiting vulnerabilities wherever they find them.
Likewise, your own product isn't a static entity; it evolves, adding new features or altering existing ones. Each change introduces potential new security gaps.
How do you stay ahead? Through relentless research. This involves:
- Threat Intelligence: Keeping an eye on the latest types of attacks, whether it's a novel form of SQL injection or a new phishing tactic.
- Internal Audits: Regularly scanning your own system for vulnerabilities. This is akin to a self-checkup, identifying the weak spots before someone else does.
- Community and Vendor Reports: Subscribing to security bulletins, whitepapers, and also vendor-specific advisories can offer valuable insights.
The objective is to continuously update your understanding of what you're up against and adjust your defenses accordingly.
{{promo}}
Close Breaches
Once you identify a vulnerability or a potential threat, the next step is to slam that door shut. You have two primary weapons in your arsenal:
- WAF Rules: Custom or managed, these rules are your first line of defense. For instance, if your research identifies a new type of XSS attack targeting JavaScript libraries you use, you can immediately implement a WAF rule to block or flag requests containing the malicious script.
- Additional Security Services: Sometimes WAF might not be enough, or it may not be the right tool for a specific type of vulnerability. In such cases, other security add-ons like Intrusion Detection Systems (IDS) or Data Loss Prevention (DLP) tools can be integrated to patch the breach.
Test
You've done your research. You've put new rules in place. But hold your horses—before switching them to "block" mode, it's crucial to test them extensively. Why? Because the worst-case scenario isn't just blocking malicious traffic; it's also blocking legitimate users from accessing your services.
Here's the standard procedure:
- Log Mode: Initially, set your new WAF rules to "log" mode. This allows you to monitor what they would block without actually blocking it.
- Traffic Analysis: Examine the logs to ensure that the rules are flagging exactly what they're supposed to flag, and nothing more.
- Fine-Tuning: If you find that legitimate requests are getting caught in the net, it's back to the drawing board to tweak your rules.
- Validation: Once you're confident that the rules are precise, switch them from "log" to "block" mode.
The Security Flywheel is an ongoing cycle. After you've researched, closed breaches, and tested, you start all over again. The Internet doesn't stand still, and neither should your security efforts.
The WAF Challenge
Even with the robust structure of a Web Application Firewall (WAF), there are obstacles to navigate.
Two of them are particularly gnarly: fine-tuning rules to perfection and managing a WAF over a multi-CDN architecture. Let's dive deep into these challenges.
1. Finding the Rule Sweet Spot
The objective here is straightforward—sort of like Goldilocks finding the porridge that's "just right." But instead of porridge, we're talking about WAF rules.
Too lax, and malicious traffic might seep through, compromising the security fortress you've been building. Too strict, and you might end up fencing off genuine users, which is bad for business and user experience.
2. Configuring and Maintaining WAF on a Multi-CDN
Multi-CDN architectures, the double-edged swords. They offer redundancy, better global reach, and load balancing but throw in a curveball when it comes to WAF configuration.
Managing WAF over a single CDN is somewhat simpler—you establish rules and policies, and you're done. However, in a multi-CDN environment, ensuring that the rules are consistently applied across all CDNs becomes a logistical nightmare.
One CDN's interpretation of a rule might differ from another's, leading to inconsistencies in how web traffic is filtered. You'll have logs and analytics scattered across different CDNs. Aggregating this data into a single, coherent view for analysis becomes an additional hurdle. Without a unified perspective, pinpointing vulnerabilities or attack patterns becomes a herculean task.
Similarly, a rule that works perfectly on one CDN may trigger false positives or negatives on another due to slight variations in how each CDN processes web traffic. These discrepancies can undermine the WAF's effectiveness, necessitating frequent rule adjustments.
WAF Threats

When you're fortifying your digital fortress with a Web Application Firewall (WAF), it's essential to know the enemy.
1. SQL Injection
SQL Injection is a classic but ever-relevant threat. It's like that old movie that people can't help but rewatch—it's too good, or in this case, too effective for attackers. SQL Injection involves inserting malicious SQL queries into an input field, tricking the database into revealing sensitive information.
Imagine a login page.
Normally, you input a username and a password, which the system verifies before letting you in. In a SQL Injection attack, instead of a legitimate username, an attacker inputs a crafted SQL query. The system, deceived, executes this query, often revealing confidential data.
WAF can detect these abnormal input patterns and block the request right at the doorstep. Custom rules can be designed to look for typical SQL injection patterns like UNION SELECT, --, or /*.
2. DDoS Attacks
Distributed Denial of Service (DDoS) attacks are the digital world's equivalent of a stampede. A horde of compromised computers overwhelms a server, rendering it incapable of handling legitimate requests.
In a DDoS attack, the attacker controls a network of zombie computers (often referred to as a botnet). These computers flood the target server with an overwhelming amount of requests, causing it to slow down or even crash.
WAFs can rate-limit incoming requests, creating a sort of queue system. Only a specific number of requests from an IP address are allowed within a given time frame.
3. XSS (Cross-Site Scripting)
Cross-Site Scripting, commonly known as XSS, is another prevalent form of web application attack. It involves injecting malicious scripts into websites viewed by other users.
In an XSS attack, the attacker inputs a malicious script into a comment section or any other user input field. When another user views this content, the script executes, often stealing cookies or login sessions.
WAFs can be configured to look for typical XSS payloads, such as <script> tags or JavaScript events like onload.
4. Zero-Day Attacks
Zero-Day Attacks are the ninjas of cyber threats—stealthy, unpredictable, and deadly. They exploit unknown vulnerabilities, giving developers zero days to fix the issue—hence the name.
Attackers discover a previously unknown vulnerability in a software or system. They exploit it before the developers have a chance to release a patch.
While it's difficult for any security system to fully protect against unknown threats, WAFs offer a layer of generalized security that can mitigate the impact. Vendor-managed rule sets frequently update to adapt to new kinds of threats, offering a dynamic defense line against evolving attack vectors.
{{promo}}
Add-On Services Co-Existing With WAF
Web Application Firewall (WAF) serves as the vanguard in your digital fortification plan, but it doesn't have to go it alone.
Think of it as the captain of a well-trained squad, each member with a specialized skill set. While WAF fends off a variety of web-based threats, several complementary services magnify its capabilities.
These add-ons amplify your security, giving you not just a shield, but a full-fledged armory.
Rate Limiting
While fast and uninterrupted service is the dream, an avalanche of incoming requests can be a nightmare. Here's where Rate Limiting shines. It acts as a pace-setter, controlling the flow of traffic to ensure your application doesn't get overwhelmed.
Rate Limiting doesn't just blindly limit the number of requests; it's more nuanced than that. This service categorizes incoming traffic based on various parameters like IP address, request type, or even the payload size. Then, it applies predefined limits to each category. For instance, you can limit non-authenticated users to 10 requests per minute while allowing 100 for authenticated ones.
Rate Limiting and WAF make a dynamic duo. WAF focuses on the content of requests, flagging or blocking malicious ones. Rate Limiting, on the other hand, focuses on the quantity. When combined, they offer a two-pronged approach: quality and quantity control. It's like having a bouncer and a ticket counter at a nightclub—each ensures a different aspect of the overall experience.
Access Rules
Access Rules are the snipers of your security setup—highly targeted and extremely effective. They allow you to set granular permissions, granting or denying access based on specific conditions such as geographic location, IP ranges, or even time of day.
Imagine you have a special promotion only available to customers in a particular country. Access Rules enable you to restrict access to that specific promotion page to IPs originating from that country. It's that precise.
WAF provides a broad-stroke approach, filtering requests based on a comprehensive rulebook. Access Rules fill in the gaps with their specificity.
If WAF is the hammer, then Access Rules are the scalpel. Both tools are essential, but for different tasks. Together, they form a more comprehensive and nuanced security strategy.
Bot Detection
Not all bots are created equal. Some are benevolent, like search engine crawlers, while others have more nefarious intentions, like scraping content or executing automated attacks. Bot Detection helps you differentiate the saints from the sinners.
Bot Detection uses a combination of heuristic analysis, behavior patterns, and known bot signatures to identify the type of bot interacting with your application. From simple CAPTCHAs to intricate challenge-based mechanisms, Bot Detection employs a wide array of tactics to distinguish human users from bots.
WAF itself can block known malicious bots based on its rulebook, but its capabilities are limited in terms of behavioral analysis. That's where Bot Detection comes in. It adds an extra layer of intelligence, enabling your security setup to adapt to more sophisticated bot-based threats.
WAF Over Multi-CDN
Setting up Multi-CDN architecture while maintaining robust security can be akin to playing 4D chess. However, when Web Application Firewalls (WAFs) enter this complex space—especially Edge WAFs—the game changes.
By operating on the edge network, closer to end-users, these specialized WAFs offer superior security.
But deploying them across multiple Content Delivery Networks (CDNs) comes with its own set of challenges and intricacies
Multi-CDN Challenges
While a single CDN environment allows for straightforward WAF configuration, a Multi-CDN ecosystem is a whole other beast. Each CDN has its own interpretation of WAF rules, which can lead to inconsistencies in security measures across the board. It's like trying to sing in harmony when everyone is reading from a different hymn sheet.
Moreover, each Edge WAF operates in isolation, unable to monitor traffic flowing through other CDNs. This is a glaring blind spot, making it difficult to have a cohesive, unified view of the overall security landscape.
One solution is to employ a third-party WAF that operates independently of the CDNs. While this approach can offer uniform security protocols across all CDNs, it adds an extra layer to the network architecture. This can sometimes adversely affect performance, creating a trade-off between security and speed.
{{promo}}
Strategies for Effective WAF Deployment in Multi-CDN Environments
Managing Web Application Firewalls (WAFs) across multiple Content Delivery Networks (CDNs) can be challenging. While some solutions might advocate for unified rule management through API integrations or by using third-party WAFs, there are limited options that truly cater to multi-CDN setups on the edge.
IO River is one of the few that stands out in this domain. With its unique offering, IO River addresses the complexities of deploying WAFs on the edge in multi-CDN environments, ensuring top-notch security without sacrificing performance.
The aim here is to ensure consistent WAF behaviour across multiple CDN vendors without adding an extra tier which all traffic should go through.
To offset the blind spots inherent in Multi-CDN environments, real-time analytics and reporting become indispensable. They provide a consolidated view of all traffic and security events, enabling quicker and more informed decision-making.
Before full-scale deployment, it's crucial to test the WAF's impact on application performance. Benchmarks should be established to measure the latency introduced by the WAF, ensuring it stays within acceptable limits.
Conclusion
In the face of all these challenges, CDN Web Application Firewalls (WAFs) emerge as both a shield and a facilitator. They stand guard, ensuring that malicious traffic is kept at bay, while also optimizing the web experience for genuine users. With features tailored to handle diverse threats, from SQL injections to DDoS attacks, WAFs are indeed a cornerstone of modern cybersecurity.




.gif)
.gif)
.gif)