Machine Learning for Fraud Detection in Streaming Services
The Netflix TechBlog
NOVEMBER 11, 2022
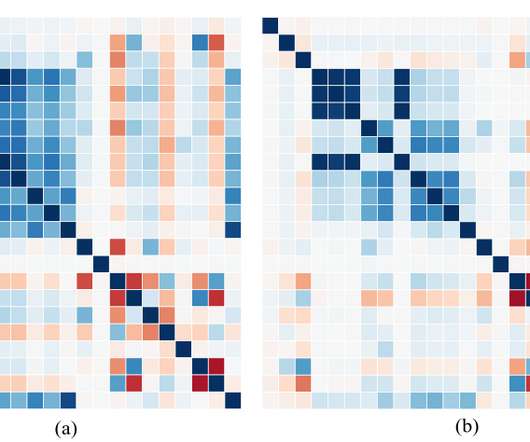
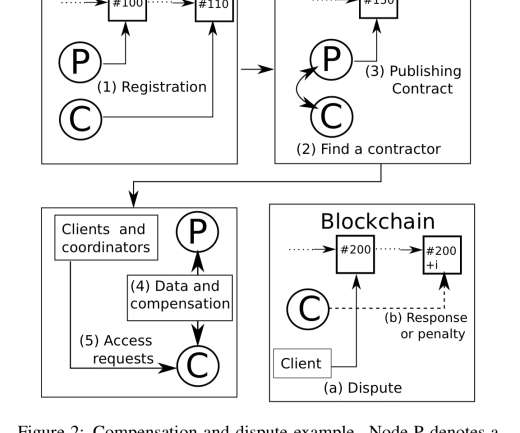
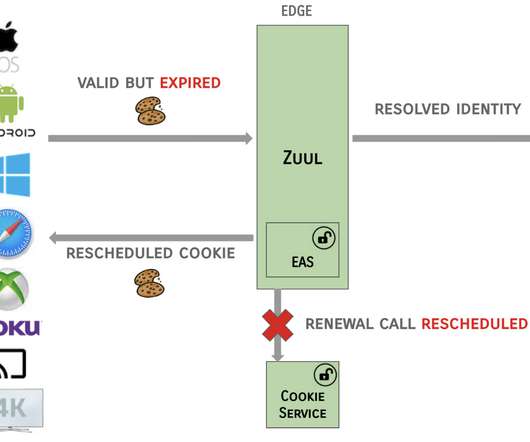
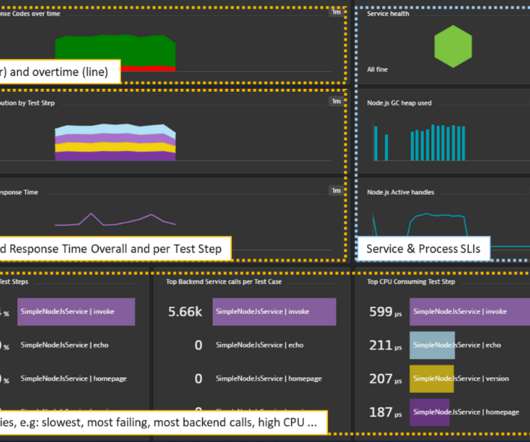
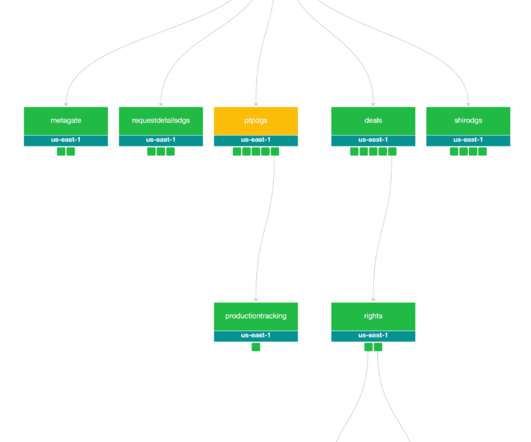
Many users across many platforms make for a uniquely large attack surface that includes content fraud, account fraud, and abuse of terms of service. There are two main anomaly detection approaches, namely, (i) rule-based, and (ii) model-based. Detection of fraud and abuse at scale and in real-time is highly challenging.






































Let's personalize your content