Securing the Keys to the Kingdom: Exploring the Depths of Privileged Access Management (PAM)
DZone
FEBRUARY 9, 2024
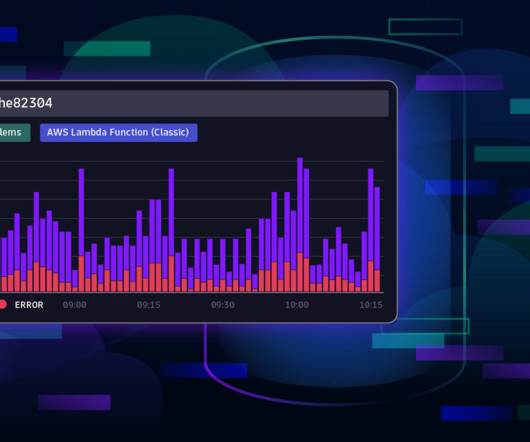
In the paradigm of zero trust architecture , Privileged Access Management (PAM) is emerging as a key component in a cybersecurity strategy, designed to control and monitor privileged access within an organization. What Is a Privileged User and a Privileged Account? What Is a Privileged User and a Privileged Account?












































Let's personalize your content