AI techniques enhance and accelerate exploratory data analytics
Dynatrace
FEBRUARY 28, 2024
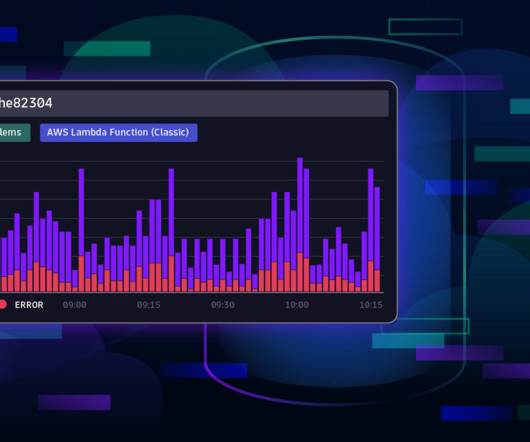
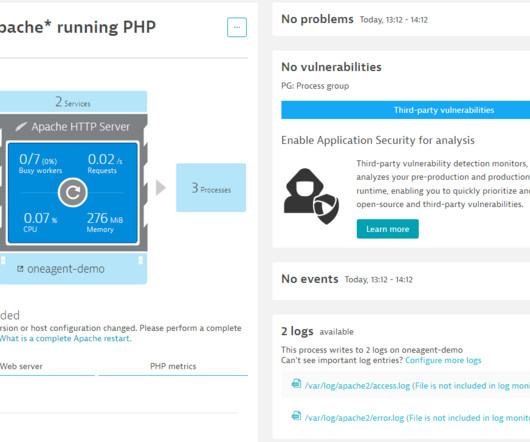
Increasingly, organizations seek to address these problems using AI techniques as part of their exploratory data analytics practices. The next challenge is harnessing additional AI techniques to make exploratory data analytics even easier. Start by asking yourself what’s there, whether it’s logs, metrics, or traces.










































Let's personalize your content