7 Tips for Effective Cybersecurity Training for Developers
DZone
JANUARY 10, 2024
Cybersecurity is an ever-present concern for organizations across all industries. Set Goals for Developers Writing code can be a time-consuming process. Threat actors continually seek ways to infiltrate businesses and sell stolen data to the highest bidder.




















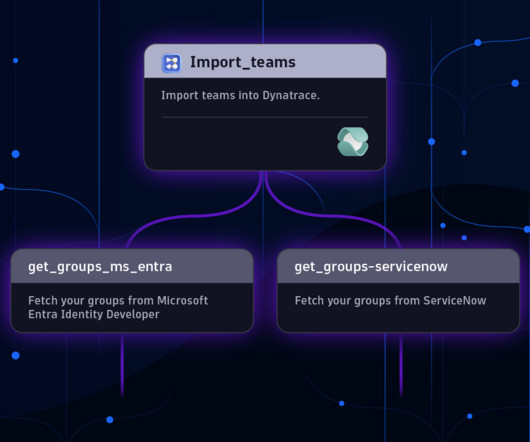

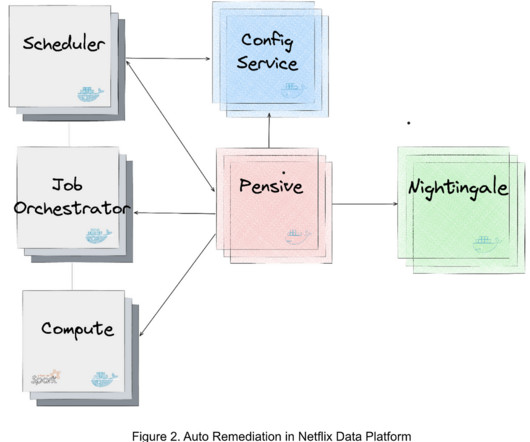



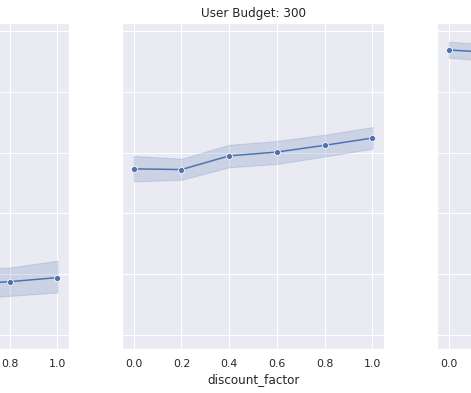












Let's personalize your content