How To Implement Video Information and Editing APIs in Java
DZone
MARCH 2, 2023
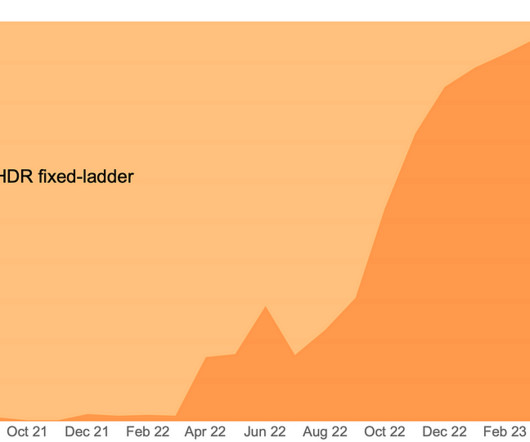
According to data provided by Sandvine in their 2022 Global Internet Phenomena Report , video traffic accounted for 53.72% of the total volume of internet traffic in 2021, and the closest trailing category (social) came in at just 12.69%.









































Let's personalize your content