Dynatrace Real User Monitoring now automatically detects CSP violations, providing insights into potential frontend application attacks. The automatic alerting and deep analysis of CSP violations helps prevent malicious attacks for all web apps, with no configuration required.
Malicious attacks like cross-site scripting can make your website unresponsive or steal data and personally identifiable information of your users.
Content Security Policy (CSP) is a browser feature that adds an extra layer of security against such threats to your web applications. CSP ensures that all scripts and plugins on your website are safe and trusted, and that all page resources, such as images and stylesheets, are loaded from trusted sources.
We’re excited to announce that Dynatrace Real User Monitoring now helps you
- automatically detect security threats and
- continuously improve your CSP policies.
Dynatrace now automatically detects all Content Security Policy violations as reported by the browser—for all your web applications—no configuration required.
Davis automatically detects security threats for all web apps
Davis, our AI-engine, automatically alerts you when it detects anomalies in your CSP violations. This means that you are always notified of any attempted attacks that cause CSP violations or of any potential misconfiguration of your CSP policies. Our Davis AI-engine unlocks these capabilities:
- Auto-baselining and smart alerting out-of-the-box for all request errors, including CSP violations
With no configuration, Davis automatically creates auto-baselines for request errors for your web applications and raises problems when anomalies are detected. - Customization for automatic alerts tailored to your requirements
If you want Davis to alert on CSP violations only, excluding all other available request error types, or if you want to want to focus on CSP violations for specific pages, Dynatrace has you covered.
You can leverage platform functionalities like calculated metrics, Multidimensional analysis for filtering errors by error type (request error codes) or resource (request error resources), and metric events for alerting to tailor alerting to your requirements. (For full details, see Configure and analyze web application errors in Dynatrace Documentation.)
Continuously improve your CSP policies with deep analysis
Every single CSP violation indicates a script, plugin, or resource that is not covered by a Content Security Policy. This can be a misconfiguration and also a potential security threat to your application.
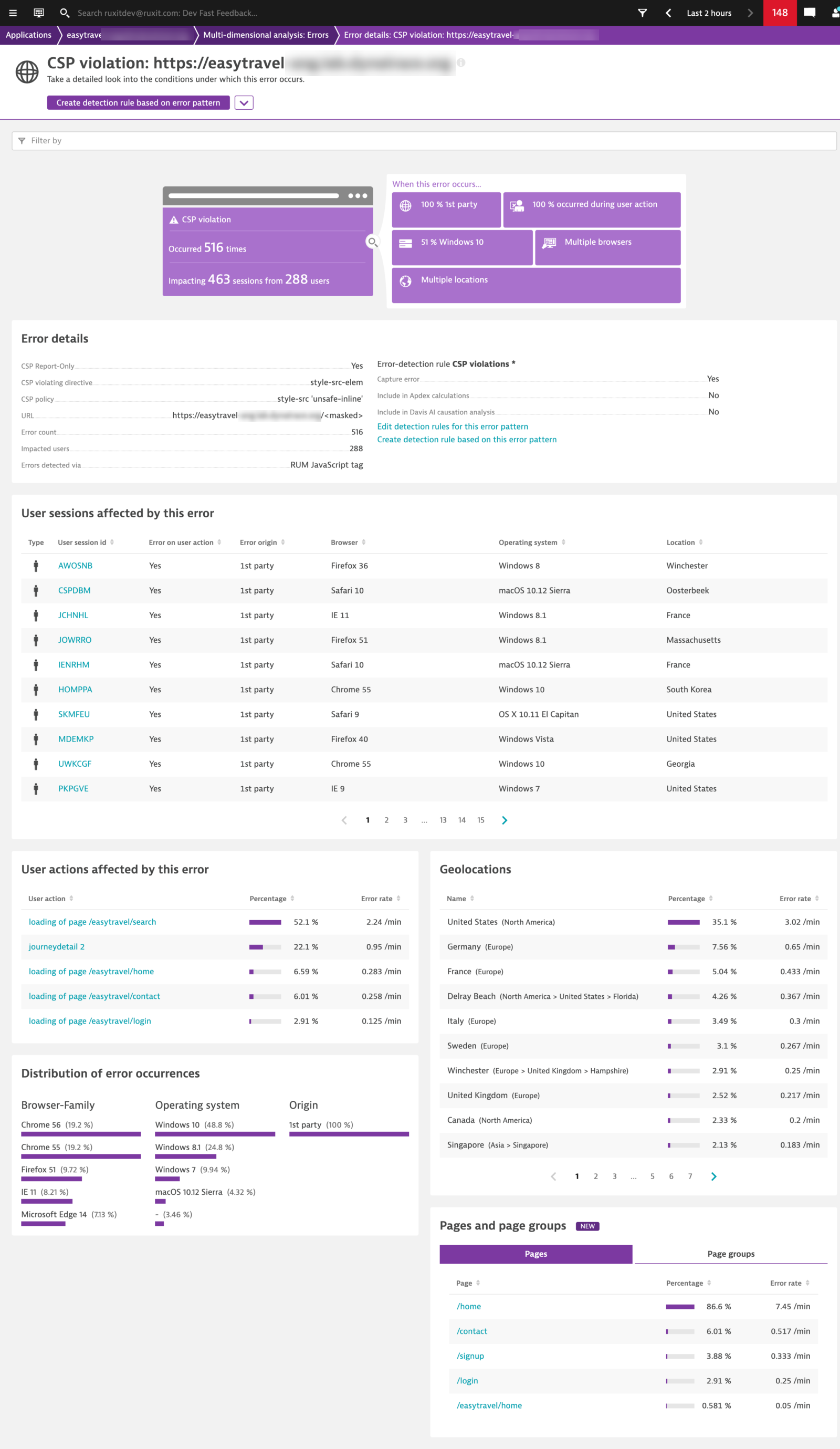
With Dynatrace you can easily identify which of your pages currently face CSP violations and then drill down to get all the information and context necessary to segment the error and fix or adapt your policies accordingly.
Besides linked user sessions, actions, and various breakdowns, we’ve also extended the error information with CSP-specific details:
- Was the violation truly enforced or was it only triggered in report-only mode, and therefore not truly enforced?
- What’s the related directive, and
- What’s the overall policy that was violated?
Get started now
CSP violations are fully available with Dynatrace version 1.217. The easiest way to find such errors is to go to your desired application’s overview page and look for CSP violations on the Top errors card (see example below). Of course you can also use CSP violations for multidimensional analysis when you filter by request error code.
Start your free trial today and gain unmatched insights into the digital experience of all your web and mobile apps.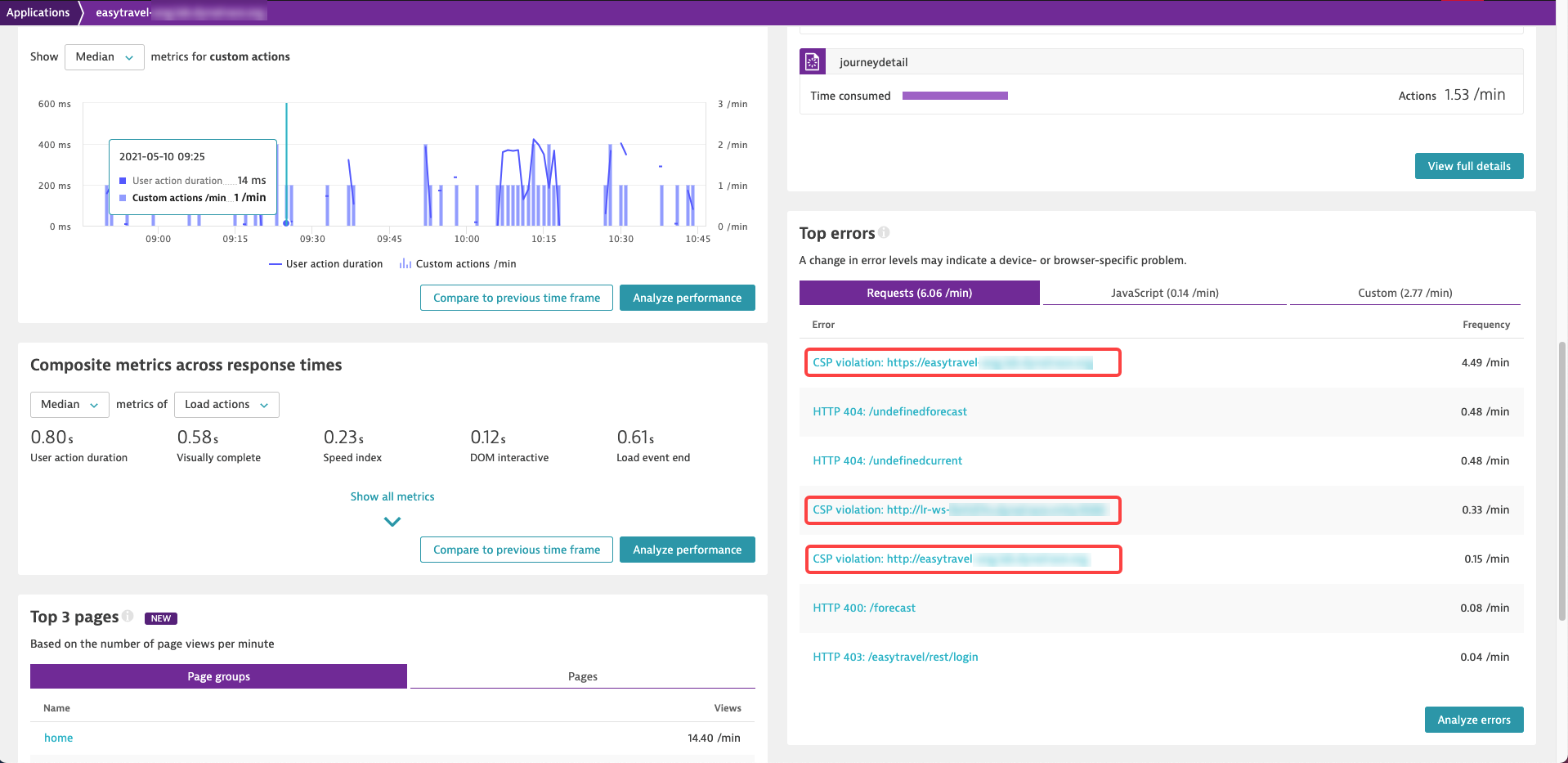
If you’re new to Dynatrace




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum