The State of DevOps Automation assessment: How automated are you?
Dynatrace
APRIL 22, 2024
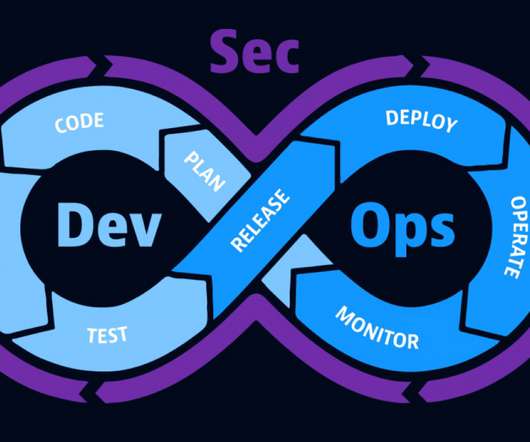
Armed with this knowledge, organizations can systematically address their weaknesses and specifically determine how to improve these areas. For this reason, teams need a comprehensive evaluation to assess their implementation of numerous facets of DevOps automation. The tool assigns every response to a question a unique point value.






















Let's personalize your content