Kubernetes in the wild report 2023
Dynatrace
JANUARY 16, 2023
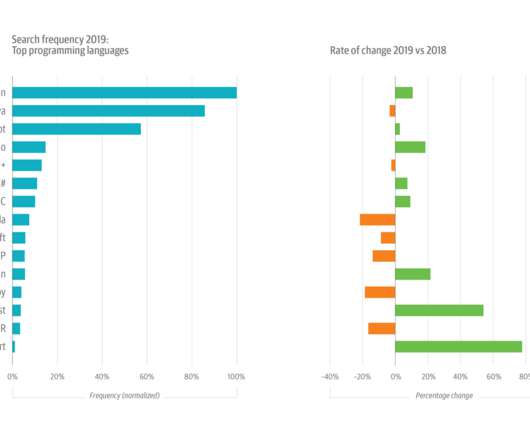
While Kubernetes is still a relatively young technology, a large majority of global enterprises use it to run business-critical applications in production. Findings provide insights into Kubernetes practitioners’ infrastructure preferences and how they use advanced Kubernetes platform technologies. Java, Go, and Node.js












































Let's personalize your content