How Virtualization Helps Security
DZone
MAY 16, 2023
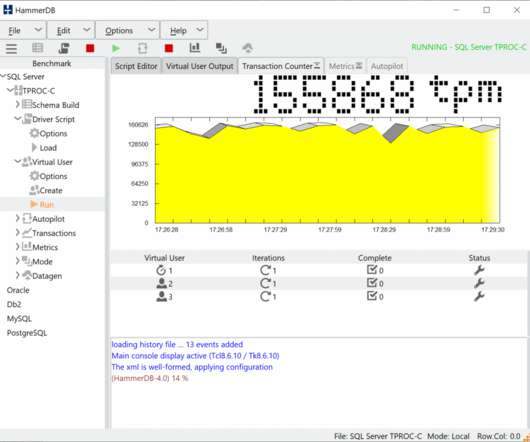
Among these are virtual tools and programs that have applications in almost every industry imaginable. One area that virtualization technology is making a huge impact is the security sector. How Is Virtualization Technology Used? Devices connect to a virtual network to share data and resources.







































Let's personalize your content