Securing the Keys to the Kingdom: Exploring the Depths of Privileged Access Management (PAM)
DZone
FEBRUARY 9, 2024
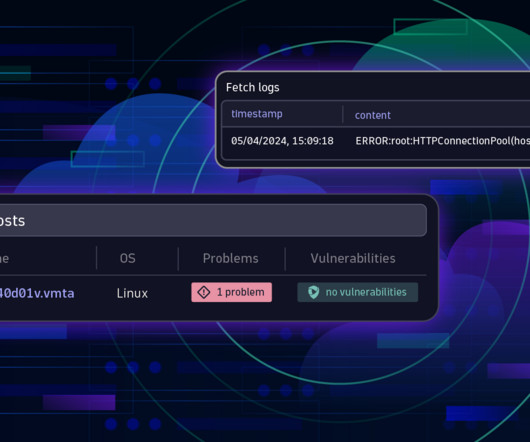
This article delves into the pivotal role of PAM in modern cybersecurity, exploring its principles, implementation strategies, and the evolving landscape of privileged access. What Is a Privileged User and a Privileged Account?













































Let's personalize your content