What is IT operations analytics? Extract more data insights from more sources
Dynatrace
MAY 1, 2023
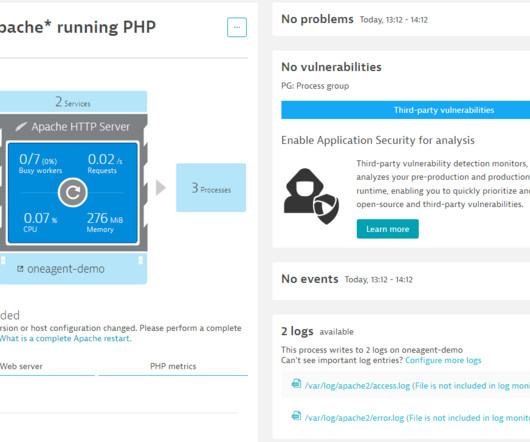
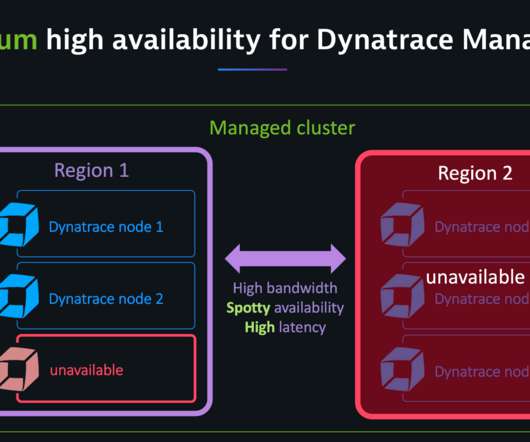
IT operations analytics is the process of unifying, storing, and contextually analyzing operational data to understand the health of applications, infrastructure, and environments and streamline everyday operations. How does IT operations analytics work? Automate analytics tools and processes.











































Let's personalize your content