Native Frame Rate Playback
The Netflix TechBlog
JUNE 5, 2023
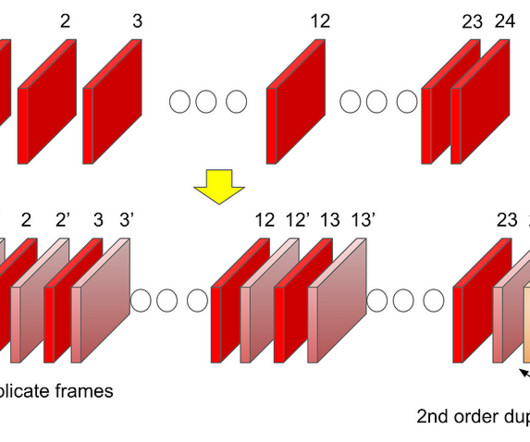
by Akshay Garg , Roger Quero Introduction Maximizing immersion for our members is an important goal for the Netflix product and engineering teams to keep our members entertained and fully engaged in our content. Leveraging a good mix of mature and cutting-edge client device technologies to deliver a smooth playback experience with glitch-free in-app transitions is an important step towards achieving this goal.














Let's personalize your content