Understanding, detecting and localizing partial failures in large system software
The Morning Paper
MARCH 15, 2020
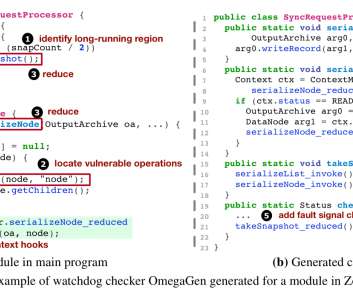
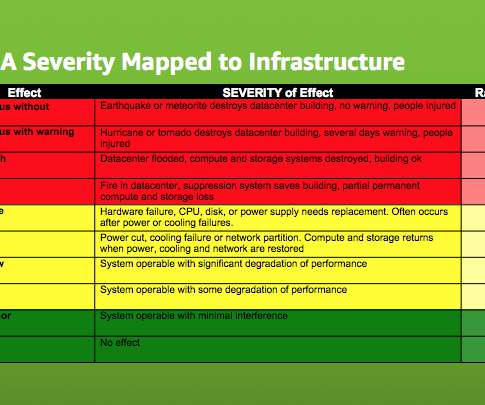
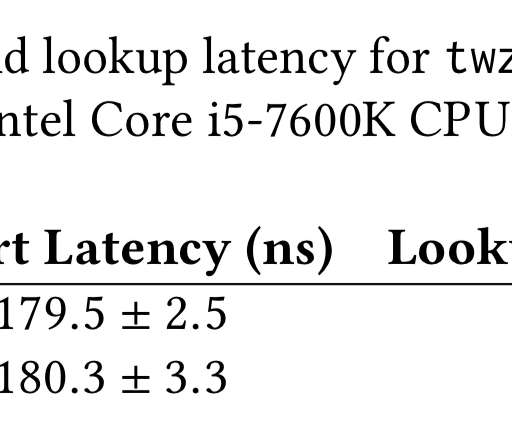
Understanding, detecting and localizing partial failures in large system software , Lou et al., Partial failures ( gray failures ) occur when some but not all of the functionalities of a system are broken. Here are the key findings: Partial failures appear throughout the release history of each system, 54% within the last three years.





























Let's personalize your content