Monitor web applications from within your corporate network
Dynatrace
JUNE 7, 2019
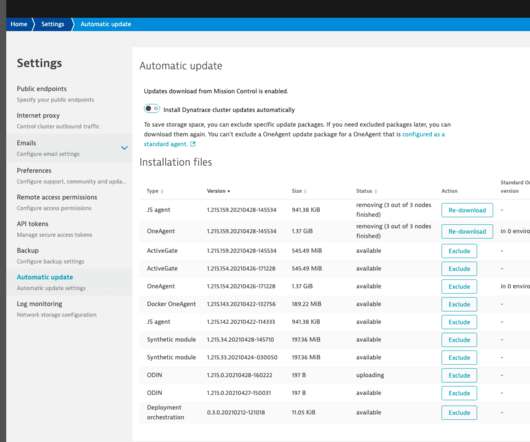
Q: Is there a plan to support more operating systems? Support for newer versions of these systems will be introduced as well. Q: Do I need a special network configuration, opening non-standard ports and/or whitelisting some addresses? A: It all depends on your internal network architecture.








































Let's personalize your content