All of Netflix’s HDR video streaming is now dynamically optimized
The Netflix TechBlog
NOVEMBER 29, 2023
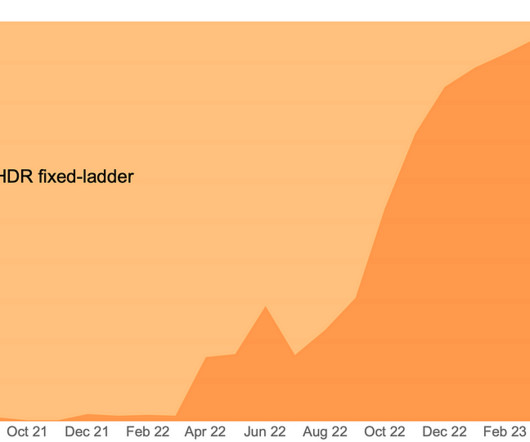
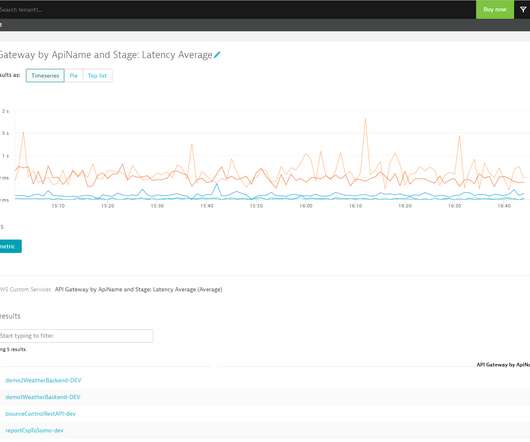
HDR was launched at Netflix in 2016 and the number of titles available in HDR has been growing ever since. As noted in an earlier blog post , we began developing an HDR variant of VMAF; let’s call it HDR-VMAF. We present two sets. The arrival of HDR-VMAF allowed us to create HDR streams with DO applied, i.e., HDR-DO encodes.






































Let's personalize your content