Mastering Kubernetes deployments with Keptn: a comprehensive guide to enhanced visibility
Dynatrace
MARCH 20, 2024
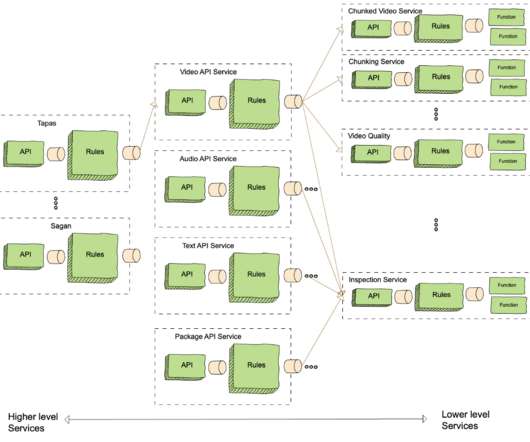
In this article, we’ll explore these challenges in detail and introduce Keptn, an open source project that addresses these issues, enhancing Kubernetes observability for smoother and more efficient deployments. Vulnerabilities or hardware failures can disrupt deployments and compromise application security.






































Let's personalize your content