Efficient SLO event integration powers successful AIOps
Dynatrace
APRIL 5, 2024
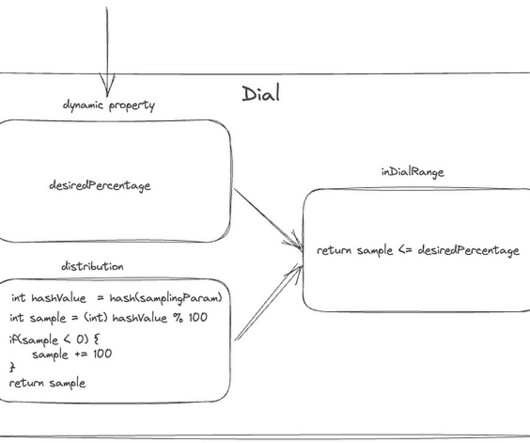
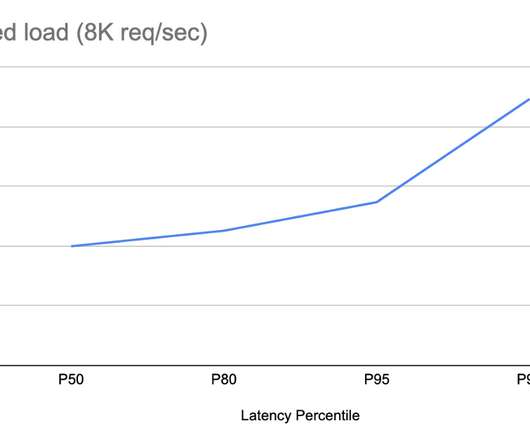
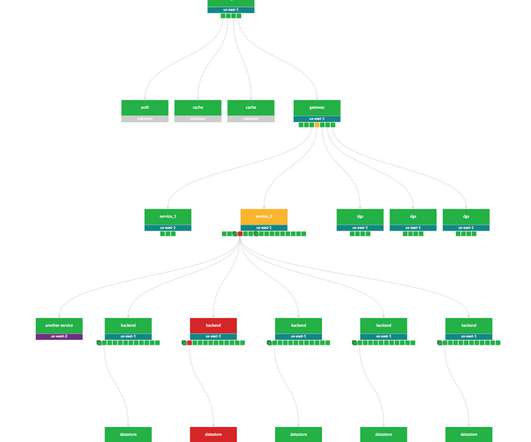
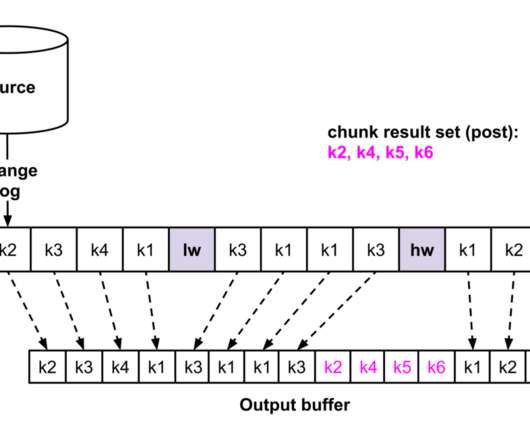
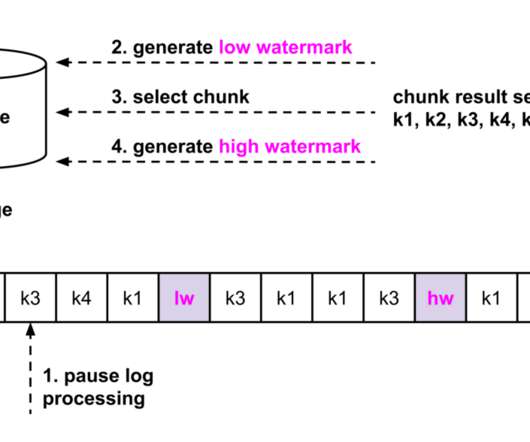
This blog post is for both novice and seasoned audiences alike. The first part of this blog post briefly explores the integration of SLO events with AI. When the SLO status converges to an optimal value of 100%, and there’s substantial traffic (calls/min), BurnRate becomes more relevant for anomaly detection.






































Let's personalize your content